Privacy Showing 14 Articles

Powered by blockchain, decentralized storage systems keep data files across geographically distributed nodes connected via P2P networking.
What Is Decentralized Storage?

Security is a must in the crypto space. Knowing the most common Bitcoin scams and how to avoid them could save you from losing your bitcoins for good.
Common Bitcoin Scams and How to Avoid Them
What is that "accept all cookies?" pop-up really asking you when you open a web page? Learn all you need to know about HTTP cookies at Binance Academy.
What Are Cookies?
End-to-end encryption turbocharges your privacy by ensuring only the intended recipient can decrypt messages you send them. Learn more at Binance Academy.
What is End-to-End Encryption (E2EE)?

A range of techniques have emerged to break the link between Bitcoin addresses. Learn more about coin mixing and CoinJoins at Binance Academy.
Coin Mixing and CoinJoins Explained

Confidential Transactions are a privacy-enhancing upgrade to cryptocurrency protocols that obfuscate the amounts sent between participants from the network.
An Introduction to Confidential Transactions

Device Fingerprinting is a powerful technique can be used for both legitimate and shady activities. Understanding their basic mechanisms is essential.
Device Fingerprinting: How Exposed Are You?

PGP has been an essential tool for data protection and is now used in a wide range of applications, providing privacy, security, and authentication.
What Is PGP?

Privacy has always been valuable within the cryptocurrency community. It is the precursor to fungibility, which is necessary for a widely used form of money
zk-SNARKs and zk-STARKs Explained

For many people, being able to connect to free internet on the go seems ideal. However, there are more risks to using public WiFi than you may realize.
Why Public WiFi Is Insecure
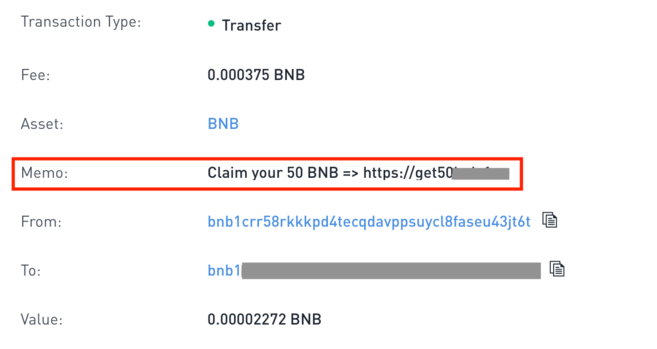
Have you received a small amount of unsolicited cryptocurrency into your wallet? You may be a victim of a Dusting Attack. Learn about dusting attacks.
What Is a Dusting Attack?
Phishing is a type of cyber attack where a malicious actor deceives people to collect their sensitive information. Learn about Phishing on Binance Academy.
What Is Phishing?
Complete guide to Keyloggers: What they are, how to protect yourself and how to detect and remove Keyloggers.
What Is a Keylogger?